 2025-11-21: Best Paper Award at iFM 2025 2025-11-21: Best Paper Award at iFM 2025Our paper "Security of the Lightning Network: Model Checking a Stepwise Refinement with TLA+" received the best paper award at the 20th International Conference on Integrated Formal Methods (iFM 2025). In this contribution, we present our method and result of a security analysis of Lightning, the protocol of the Lightning Network. |
 2025-11-05: Successful PhD Graduation - Marc Leinweber 2025-11-05: Successful PhD Graduation - Marc LeinweberOur colleague Marc Leinweber successfully defended his doctoral dissertation on November 5, 2025. |
 2025-10-17: Talk “Eventually Consistent Access Control” at the Matrix Conference 2025 2025-10-17: Talk “Eventually Consistent Access Control” at the Matrix Conference 2025We were accepted with the talk „Eventually Consistent Access Control: Practical Insights on Matrix from Decentralized Systems Theory” at the Matrix Conference 2025 in Strasbourg. The talk gives an overview on the decentralized systems foundations relevant for Matrix, and summarizes our research on Matrix during the last years. The recording is freely accessible. |
 2025-07-29: Poster "Can a Large Language Model Keep My Secrets? A Study on LLM-Controlled Agents" 2025-07-29: Poster "Can a Large Language Model Keep My Secrets? A Study on LLM-Controlled Agents"We presented our publication "Can a Large Language Model Keep My Secrets? A Study on LLM-Controlled Agents" as a poster at this year's ACL Student Research Workshop in Vienna, Austria. We explore various approaches of automating access control decisions using LLMs. We are able to show that current LLMs are somewhat capable of performing access control tasks, while we further increase the performance by fine-tuning a model on synthetic data. |
 2025-07-08: Publication „Mitigation of Transaction Exclusion in Ethereum” 2025-07-08: Publication „Mitigation of Transaction Exclusion in Ethereum”We presented our publication “A Policy-Based Mitigation of Transaction Exclusion in Ethereum” at this year’s ACM Symposium on Access Control Models and Technologies in Stony Brook, New York, USA. In this work, we demonstrate how users can register desired policies in Ethereum, which are then enforced at the protocol level. Furthermore, we propose a concrete policy that makes transaction censorship economically unattractive. |
 2025-06-07: Publication “Eventually Consistent Access Control” 2025-06-07: Publication “Eventually Consistent Access Control”We could present our publication “To the Best of Knowledge and Belief: On Eventually Consistent Access Control” on this year's ACM Conference on Data and Application Security and Privacy (CODASPY) in Pittsburgh, Pennsylvania. At the example of decentralized communication systems like Matrix, we showed that traditional conceptual models of access control are insufficient, and present “Eventually Consistent Access Control” as alternative. The article is freely available as Open Access under CC-BY. |
 2025-04-18: Publication “Price Oracle Accuracy Across Blockchains” 2025-04-18: Publication “Price Oracle Accuracy Across Blockchains”We presented our new publication "Price Oracle Accuracy Across Blockchains: A Measurement and Analysis" at this year's "Workshop on Cryptoasset Analytics". Using the example of Chainlink, the paper examines how accurately price data from centralized trading venues is mapped on different blockchain systems and which trade-offs result from configurations of heartbeat and threshold. |
 2025-04-18: Publication „Price Oracle Accuracy Across Blockchains“ 2025-04-18: Publication „Price Oracle Accuracy Across Blockchains“We presented our new publication "Price Oracle Accuracy Across Blockchains: A Measurement and Analysis" at this year's "Workshop on Cryptoasset Analytics". Using the example of Chainlink, the paper examines how accurately price data from centralized trading venues is mapped on different blockchain systems and which trade-offs result from configurations of heartbeat and threshold. |
 2025-04-10: Publication “Proof-Carrying CRDTs” 2025-04-10: Publication “Proof-Carrying CRDTs”We have presented our new publication “Proof-Carrying CRDTs allow Succinct Non-Interactive Byzantine Update Validation” on this year's Workshop on Principles and Practice of Consistency for Distributed Data. In this work, Conflict-Free Replicated Data Types (CRDTs) are combined first-time with non-interactive cryptographic proofs, as they are known from the zero-knowledge field. The article is freely available as Open Acces under CC-BY. |
 2024-12-20: Matrix Salon Podcast: Florian Jacob 2024-12-20: Matrix Salon Podcast: Florian JacobFlorian Jacob, a member of our research group, was a guest on the latest episode of the Matrix Salon podcast, where he talked about his research on the security and resilience of the Matrix network and his life as a Ph.D. student. |
 2025-03-17: ROBUST Workshop in Karlsruhe 2025-03-17: ROBUST Workshop in KarlsruheThe ROBUST Workshop on Byzantine Fault Tolerance und State Machine Replication takes place with us at KIT in Karlsruhe this year. This workshop aims to bring together leading minds in our field to explore and discuss current and preliminary work with open questions in substantial depth. The event on March 17 and 18, 2025 is planned from lunch to lunch so that there is time to arrive and depart on the same days. The Call for Contributions as well as additional information is found on: ROBUST 2025 |
| 2025-03-17: ROBUST2025 Workshop Wir veranstalten 2025-03-17 und 2025-03-18 den ROBUST 2025 workshop. |
 2024-11-22: Talk at Bitcoin Research Day 2024-11-22: Talk at Bitcoin Research DayAt this year's Bitcoin Research Day, Hannes Hartenstein and Matthias Grundmann gave a talk titled "From Monitoring Bitcoin to Verifying Lightning: Modeling Aspects of the Bitcoin Universe". In particular, they presented our research on monitoring the P2P network of Bitcoin and on verification of the Lightning Network's protocol and discussed it with the participants. |
 2024-11-14: SofDCar Tech & Results Summit 2024-11-14: SofDCar Tech & Results SummitThe results of the BMWK-supported project SofDCar (Software-Defined Car) were presented to the public today at a technical expo in the Arena2036 in Stuttgart. Oliver Stengele was there and presented the project contributions of the research group to interested visitors. Within SofDCar, we examined the use of decentralized systems like Ethereum and the InterPlanetary File System to make the cooperation of parties along software supply chains more traceable and secure. |
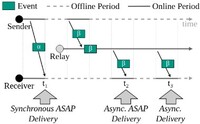 2024-12-12: Publication “ReP2P Matrix” 2024-12-12: Publication “ReP2P Matrix”While there are already various proposals for peer-to-peer communication for the decentralized messaging middleware Matrix, these proposals require that the receiver and the originator are simultaneously online. We introduce relay-enhanced P2P Matrix (ReP2P Matrix) in order to improve message delivery between peers that are online at different times. We present our new publication on this topic, ReP2P Matrix: Decentralized Relays to Improve Reliability and Performance of Peer-to-Peer Matrix, on the first Decentralization of the Internet Workshop of this year's ACM CoNEXT. The publication is available as open access under CC-BY. |
 2024-06-26: Publication “How to Raise a Robot” 2024-06-26: Publication “How to Raise a Robot”To support us in our daily lives, future humanoid assistant robots need both a certain degree of autonomy to learn and explore, but must also adhere to certain constraints. Constrained planning is a problem especially for otherwise promising approaches based on neural networks - while symbolic approaches are very good at adhering to constraints, but have trouble with complex, new environments. New developments in the area of neuro-symbolic AI would revolutionize constrained task planning. On this year's Symposium on Access Control Models and Technologies, we have presented our BlueSky publication “How to Raise a Robot - A Case for Neuro-Symbolic AI in Constrained Task Planning for Humanoid Assistive Robots” on that topic. The publication is freely available as open access under CC-BY. |
 2024-04-22: Publication “Logical Clocks and Monotonicity for Byzantine-Tolerant Replicated Data Types” 2024-04-22: Publication “Logical Clocks and Monotonicity for Byzantine-Tolerant Replicated Data Types”We presented our new publication “Logical Clocks and Monotonicity for Byzantine-Tolerant Replicated Data Types” at this year's Workshop on Principles and Practice of Consistency for Distributed Data. In the paper, we decompose Matrix and other autonomous decentralized systems into their order-theoretic foundations. We show that the decomposition allows to analyze Byzantine fault tolerance on the basis of the order-theoretic property of monotonicity. The article is freely available as open access under CC-BY |
 04/04/2024: DSN takes part at Bitcoin Research Day 2024 04/04/2024: DSN takes part at Bitcoin Research Day 2024At the Bitcoin Research Day in Fall 2024 in New York, Prof. Dr. Hannes Hartenstein and Matthias Grundmann will give a talk about our research. The talk is titled "From Monitoring Bitcoin to Verifying Lightning: Modeling Aspects of the Bitcoin Universe". Find more information at brd.chaincode.com. |
 2023-12-15: „How to Raise a Robot” - Extended Version on arXiv 2023-12-15: „How to Raise a Robot” - Extended Version on arXivFor our SACMAT poster, there is now a follow-up extended version on arXiv under the subtitle “A Case for Neuro-Symbolic AI in Constrained Task Planning for Humanoid Assistive Robots”. We report on new experiments with the unification of robot task planning and access control via Large Language Models, and show how different levels of neuro-symbolic integration can further strengthen this unification. |
 10/10/2023: "Let It TEE" - Publication at DISC'23 10/10/2023: "Let It TEE" - Publication at DISC'23At the 37th International Symposium on Distributed Computing (DISC'23), October 9-13, 2023, in L'Aquila, Italy, we presented our work Let It TEE. We showed that the consensus algorithm DAG-Rider can be transformed using Trusted Execution Environments, such as Intel SGX, such that up to 49% of protocol participants can be malicious while progress can still be made. |
 08/06/2023: „How to Raise a Robot“ – Poster at SACMAT'23 08/06/2023: „How to Raise a Robot“ – Poster at SACMAT'23During the 28th ACM Symposium on Access Control Models and Technologies at the Fondazione Bruno Kessler in Trento, Italy, we have presented our poster „How to Raise a Robot - Beyond Access Control Constraints in Assistive Humanoid Robots”. In the poster, we discuss how humanoid assistive robots can be granted both the necessary level of autonomy for their versatile learning and action capabilities, and how the robots can still learn to respect various constraints such as access control and beyond. In addition to the poster and poster abstract, the publication also includes the presentation video. |
 05/22/2023: Successful PhD Graduation - Oliver Stengele 05/22/2023: Successful PhD Graduation - Oliver StengeleToday, our staff member Oliver Stengele successfully defended his dissertation. For his work titled "Decentralizing Software Identity Management", Oliver researched approaches that enable developers to sovereignly establish and manage unique identities for software. Additionally, he implemented a digital time capsule on the Ethereum blockchain and employed it as part of an independent review process. We congratulate our colleague! |
 04/05/2023: Publication “On Extend-Only Directed Posets and Derived Byzantine-Tolerant Replicated Data Types” 04/05/2023: Publication “On Extend-Only Directed Posets and Derived Byzantine-Tolerant Replicated Data Types”We present our new publication “On Extend-Only Directed Posets and Derived Byzantine-Tolerant Replicated Data Types” at this year's Workshop on Principles and Practice of Consistency for Distributed Data. In the paper, we show a new formalization of the decentralized Matrix system using directed partially-ordered sets, which allow a more extensive model than previous approaches based on directed acyclic graphs. The Extended Version on Arxiv is freely available already. |
 04/13/2023: DSN at "Meet the Chairs" 04/13/2023: DSN at "Meet the Chairs"The research group presented itself at "Meet the Chairs" as part of the Master O-Phase, organized by the Fachschaft Mathematik/Informatik, with a Poster, our Bitcoin Monitoring, and candy. We are grateful for the good organization and the stimulating conversations and look forward to next time. |
 11/15/2022: Job offer for PhD students/research assistants (f/m/d) in science on the topic: Theory and applications of decentralized systems. 11/15/2022: Job offer for PhD students/research assistants (f/m/d) in science on the topic: Theory and applications of decentralized systems.For various application-oriented research activities in the areas of automotive software management, assistive humanoid robotics, and mobility-as-a-service systems, the Decentralized Systems and Network Services research group has several openings for PhD students/research assistants interested in research that combines theory and practice. Research activities focus on the design and analysis of decentralized methods for identity and access management, payments, and secure and privacy-friendly data exchange. Her/his work is part of a larger research project and offers the opportunity for a PhD. For more information and how to contact us, please visit the Human Resources Services page. |
 10/15/2022: Job offer for a PhD student/research assistant (f/m/d) in science on the topic: procedures for information security and privacy in humanoid assistance robotics. 10/15/2022: Job offer for a PhD student/research assistant (f/m/d) in science on the topic: procedures for information security and privacy in humanoid assistance robotics.The research group Decentralized Systems and Network Services is looking for a new research associate with a focus on the design and investigation of identity and access management methods as well as secure and privacy-compliant communication and data storage. Special attention is given to specification, implementation and evaluation of methods for networked and decentralized systems, in particular the Internet of Things, and associated middleware components. Her/his work is part of a larger research project and offers the opportunity for a PhD. For more information and how to contact us, please visit the Human Resources page. |
 2022-07-28: Blue Sky Paper on the Combination of Access Control and Assistive Humanoid Robotics 2022-07-28: Blue Sky Paper on the Combination of Access Control and Assistive Humanoid RoboticsIn the not too distant future, assistive humanoid robots will provide versatile assistance for coping with everyday life. In their interactions with humans, not only safety, but also security and privacy issues need to be considered. We therefore argue that it is time to bring task planning and execution as a well-established field of robotics with access and usage control in the field of security and privacy closer together. As part of the JuBot Project, we do research on those issues together with the H2T research group. Our first paper with the title BlueSky: Combining Task Planning and Activity-Centric Access Control for Assistive Humanoid Robots published on SACMAT'22 is now freely available as Open Acces. |
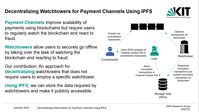 2022/07/11: Paper on Decentralization of Watchtowers at DINPS'22 Workshop 2022/07/11: Paper on Decentralization of Watchtowers at DINPS'22 WorkshopPayment Channels enable scalable payments on blockchains but require that users are regularly online to defend their channels against fraud. This task can be outsourced to third parties, so called watchtowers. At the DINPS'22 workshop, we presented an idea to decentralize watchtowers so that users do not need to trust specific employed watchtowers but a user can be defended by any watchtower. |
 2022/06/23: Talk and Paper on Decentralized ticket systems for Mobility-as-a-Service 2022/06/23: Talk and Paper on Decentralized ticket systems for Mobility-as-a-ServiceMobility-as-a-Service is in the focus of public and private actors as a development step of public transport. We have investigated which disadvantages arise in such a system due to central providers and how these disadvantages can be compensated by decentralization. We presented our current findings as well as open issues for ongoing and future research at the "14. Wissenschaftsforum Mobilität" in Duisburg in June 2022. |
 06/22/2022: Job offer for an:n academic:staff:member (f/m/d) on the topic: information security and privacy procedures in humanoid assistance robotics. 06/22/2022: Job offer for an:n academic:staff:member (f/m/d) on the topic: information security and privacy procedures in humanoid assistance robotics.The research group Decentralized Systems and Network Services is looking for a new academic staff member with a research focus on the design and investigation of identity and access management methods as well as secure and privacy-compliant communication and data storage. Special attention is given to specification, implementation, and evaluation of methods for networked and distributed systems, in particular the Internet of Things, and associated middleware components. Her work is part of a larger research project. Further information and contact details can be found on the Human Resources page. |
 2022/05/11: Paper on P2P network of Bitcoin at Financial Cryptography and Data Security 2022 2022/05/11: Paper on P2P network of Bitcoin at Financial Cryptography and Data Security 2022The number of peers in the P2P network of Bitcoin is difficult to measure. Together with two students we developed a method to estimate the number of active peers in the network - including reachable and unreachable peers. At the Financial Cryptography and Data Security 2022 we published results of applying this method to data collected through our Bitcoin Monitoring. |
 2022/05/04: Paper and Poster at IEEE ICBC 2022 2022/05/04: Paper and Poster at IEEE ICBC 2022We presented a short paper about insights into the Bitcoin P2P network at the IEEE International Conference on Blockchain and Cryptocurrency in May 2022. We show for example that the current connection capacity of a majority of the peers is fully used. Matthias Grundmann also presented a poster in which we show how security properties of payment channel protocols can be verified. |
 2022/04/07: CBT 2022 2022/04/07: CBT 2022The "6th International Workshop on Cryptocurrencies and Blockchain Technology (CBT 2022)" will be held again in conjunction with the "European Symposium on Research in Computer Security (ESORICS)" in September. Hannes Hartenstein is a member of the program committee. The Call for Papers can be found here. |
 30.12.2021: Publication "ETHTID: Deployable Threshold Information Disclosure on Ethereum" 30.12.2021: Publication "ETHTID: Deployable Threshold Information Disclosure on Ethereum"At the 3rd IEEE International Conference on Blockchain Computing and Applications (BCCA 2021) in November, Oliver Stengele presented the paper "ETHTID: Deployable Threshold Information Disclosure on Ethereum", which is now available in IEEE Xplore. The paper is the result of a cooperation with the Cryptography and Security Group of Prof. Müller-Quade and was available as a preprint since June. In this work, we show that independently generated statements can be published to a blockchain in a temporally coordinated way through a decentralized mechanism. |
 2021/11/25: Research Project Software-Defined Car 2021/11/25: Research Project Software-Defined CarThe research group Decentralized Systems and Network Services contributes to the research project Software-Defined Car (SofDCar). For more information on the project see the corresponding press release. |
 29.09.2021: Presentation at BRAINS'21 29.09.2021: Presentation at BRAINS'21At the 3rd Conference on Blockchain Research & Applications for Innovative Networks and Services, Oliver Stengele (Research Group DSN) and Sebastian Friebe (Research Group Telematics) presented a Case Study on coupling Smart Contract applications which resulted from a cooperation within KASTEL. |
 30.09.2021: Presentation at TLA+ Conference 2021 30.09.2021: Presentation at TLA+ Conference 2021At the TLA+ Conference 2021, Matthias Grundmann presented a specification of payment channels in TLA+ and how this specification can be used to specify security properties for payment channels and verify them. |
 2021/07/22: Student assistants wanted! 2021/07/22: Student assistants wanted!The research group Decentralized Systems and Network Services in cooperation with the KASTEL Mobility Lab is looking for three student assistants to build up a team for server administration, software development and experiment execution. Further information can be found here. |
 2021/05/04: Job offer for a scientific staff member (f/m/d) 2021/05/04: Job offer for a scientific staff member (f/m/d)The research group Decentralized Systems and Network Services is looking for a new academic staff member with the research focus "Information Security in Decentralized Systems for Networked Mobility". The possibility of pursuing a doctoral degree is given. Further information and contact details can be found on the Human Resources page. |
In the coming summer term, we once again offer our Hot Topics seminar with mixed topics around decentralized systems (registration via Wiwi-Portal). We are also involved with the "Internet and Society" seminar (registration via Wiwi-Portal). Both seminars allow presentation and seminar paper in English. |
 2021/03/02: Seminar "Research Focus Class: Blockchain und Payment Channel Networks" in Summer Term 2021 2021/03/02: Seminar "Research Focus Class: Blockchain und Payment Channel Networks" in Summer Term 2021In the upcoming semester, we offer a new course: The Research Focus Class, that combines a seminar with a lecture. In the summer term 2021 we will address aspects of the highly relevant and up-to-date area of Blockchain and Payment Channel Networks. In the lecture as the first part of the course, we will teach basics in this area and in the second part of the course, the seminar, students will work on advanced topics. Register here. The concept of our course is inspired by the same-titled series of COMSYS at the RWTH Aachen. |
 2021-02-22: Publication of the “Analysis of the Matrix Event Graph Replicated Data Type” 2021-02-22: Publication of the “Analysis of the Matrix Event Graph Replicated Data Type”In the Open Access journal IEEE Access, our article Analysis of the Matrix Event Graph Replicated Data Type was published. With the aim of application in decentralized publish-subscribe systems, in the paper, we extract and analyze the Matrix Event Graph(MEG) from the Matrix middleware, which is primarily used there to depict the causal history of chat messages. We show that the MEG is a so-called Conflict-Free Replicated Data Type, and thereby provides Strong Eventual Consistency. In addition, we show that the MEG, via its reduced notion of consistency when compared to traditional Distributed Ledger Technologies, can cope with environments where the majority of the participants exhibit byzantine faults. We close the article with an analysis of the scalability in form of the number of parallel causal chains in the MEG, for which we can expect an almost optimal evolution according to our results. |
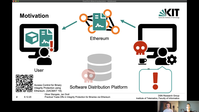 2020/11/27: Demonstrator at the ACM/IFIP Middleware 2020/11/27: Demonstrator at the ACM/IFIP MiddlewareWe present a demonstration titled Practical Trade-Offs in Integrity Protection for Binaries via Ethereum at this year's ACM/IFIP Middleware (Video). We show the practicability of our concept and how revocations of software binaries can be communicated to users in a timely manner. We also briefly touch on trade-offs that arise in a practical deployment. |
 2020/10/16: Presentations at Virtual Zeek Week 2020 2020/10/16: Presentations at Virtual Zeek Week 2020At Virtual Zeek Week 2020, we presented the Emojifier and the current state of our work on the Packet Analyzer Framework for Zeek. The framework enables the flexible addition of protocols at lower network layers and thus opens up new possibilities for monitoring networked systems, for example in the context of critical infrastructures. |
 16.10.2020: Präsentationen auf der Virtual Zeek Week 2020 16.10.2020: Präsentationen auf der Virtual Zeek Week 2020Auf der Virtual Zeek Week 2020 präsentierten wir den Emojifier sowie den aktuellen Stand unserer Arbeiten am Packet Analyzer Framework für Zeek. Das Framework ermöglicht die flexible Ergänzung von Protokollen unterer Netzwerkschichten und eröffnet so neue Möglichkeiten für das Monitoring vernetzter Systeme, zum Beispiel im Kontext kritischer Infrastrukturen. |
 2020/09/09: Publication on "Fundamental Properties of the Layer Below a Payment Channel Networks" 2020/09/09: Publication on "Fundamental Properties of the Layer Below a Payment Channel Networks"We present our publication Fundamental Properties of the Layer Below a Payment Channel Network (Abstract-Video) at the 4th International Workshop on Cryptocurrencies and Blockchain Technology (CBT 2020). We show which properties are required for the first layer below a payment channel network and that a first layer cannot only be implemented by a blockchain. |
 Nachklausur IT-Sicherheitsmanagement für vernetzte Systeme im SS 20 Nachklausur IT-Sicherheitsmanagement für vernetzte Systeme im SS 20Die Nachklausur wird am 27.07. um 8:00 Uhr im Tulla-Hörsaal (Geb 11.40) stattfinden. Die Anmeldung im CAS ist ab jetzt bis zum 20.07., 23:59 Uhr möglich. Eine Online-Abmeldung ist bis zum 26.07. um 23:59 Uhr möglich. Für die Klausur sind keine Hilfsmittel (außer einem Wörterbuch) zugelassen. Sollten Sie ein Wörterbuch verwenden wollen, muss dieses beim Einlass von der Aufsicht überprüft werden. Weitere Informationen zur Koordinierung des Einlasses und zur Beachtung des Infektionsschutzes werden rechtzeitig vor der Klausur an die Teilnehmer/-innen übermittelt. |
Die Nachklausur wird am 27.07. um 8:00 Uhr im Tulla-Hörsaal (Geb 11.40) stattfinden. Die Anmeldung im CAS ist ab jetzt bis zum 20.07., 23:59 Uhr möglich. Eine Abmeldung ist bis zum 26.07. um 23:59 Uhr möglich. Für die Klausur sind keine Hilfsmittel (außer einem Wörterbuch) zugelassen. Sollten Sie ein Wörterbuch verwenden wollen, muss dieses beim Einlass von der Aufsicht überprüft werden. Weitere Informationen zur Koordinierung des Einlasses und zur Beachtung des Infektionsschutzes werden rechtzeitig vor der Klausur an die Teilnehmer/-innen übermittelt. |
 2020/06/19: 4th International Workshop on Cryptocurrencies and Blockchain Technology (CBT 2020) 2020/06/19: 4th International Workshop on Cryptocurrencies and Blockchain Technology (CBT 2020)On September, 17th and 18th the 4th International Workshop on Cryptocurrencies and Blockchain Technology" (CBT 2020) will take place, co-located with ESORICS 2020. Prof. Hartenstein will serve on the program commitee of the workshop. We encourage submissions related to cryptocurrencies and blockchain technology (see call for papers). |
| 2020/06/11: Matrix Decomposition: Analysis of an Access Control Approach on Transaction-based DAGs without Finality vorgestellt auf der SACMAT 2020 At the 25th ACM Symposium on Access Control Models and Technologies, we presented our paper Matrix Decomposition: Analysis of an Access Control Approach on Transaction-based DAGs without Finality. In this paper, we decompose, abstract and analyze the access control approach of the Matrix middleware for decentralized applications, and show that Matrix can be seen as a Distributed Ledger Technology without strict Consensus. This has interesting consequences when compared to traditional access control approaches, which we discuss as well. The talk was recorded, and will be publishde by SACMAT at a later date. The publication was also the topic of this blog post on Matrix.org, which covers the Matrix.org view on our findings. |
| Matrix Decomposition: Analysis of an Access Control Approach on Transaction-based DAGs without Finality presented at SACMAT At the 25th ACM Symposium on Access Control Models and Technologies, we presented our paper Matrix Decomposition: Analysis of an Access Control Approach on Transaction-based DAGs without Finality. In this paper, we decompose, abstract and analyze the access control approach of the Matrix middleware for decentralized applications, and show that Matrix can be seen as a Distributed Ledger Technology without strict Consensus. This has interesting consequences when compared to traditional access control approaches, which we discuss as well. The talk was recorded, and will be publishde by SACMAT at a later date. The publication was also the topic of this blog post on Matrix.org, which covers the Matrix.org view on our findings. |
 2020/04/06: Awarded Zeek Packages 2020/04/06: Awarded Zeek PackagesThe Zeek package contest honors extensions for the well-known network monitoring tool Zeek. In the Zeek Package Contest 2019, two extensions developed in the research group were recognized. The Emojifier won the category for Zeek 3.0 compatible extensions and the Intel-Limiter was awarded the second place in the main competition. |
 2020/04/01: COVID-2019 Pandemic: Online Teaching 2020/04/01: COVID-2019 Pandemic: Online TeachingThe information on online teaching due to the COVID 19 pandemic can now be found on our page Teaching. |
 Understanding Blockchains: Lecture at VDE Mittelbaden on 24/03/2020 (cancelled) Understanding Blockchains: Lecture at VDE Mittelbaden on 24/03/2020 (cancelled)Prof. Hannes Hartenstein will give a presentation at Hochschule Karlsruhe on the 24th of March 2020 at 5:30 PM with the title "Geglückte Verkettung von Zuständen: Blockchains Verstehen" (in German). In this lecture, the basic elements of blockchains will be explained in a generally understandable way and insights into the communication behavior in the Bitcoin network will be presented. Then, existing challenges and approaches to solutions, especially with regard to security and scalability, as well as the automatic execution of contracts on blockchains ("Smart Contracts") are considered. The lecture concludes with a socio-technical view on questions of power in blockchain-based systems. Further Informations at VDE Mittelbaden. |
 Access Control Systems Lab: Best Lab SS2019 Access Control Systems Lab: Best Lab SS2019On the basis of the teaching evaluation of KIT carried out every semester, the KIT Faculty of Informatics awarded our "Praktikum Access Control Systems" as best lab for the summer semester 2019. Many thanks to the students for this evaluation result! |
 2020/01/14: New date for written exam "Angewandte Themen für das Informatik-Lehramt" 2020/01/14: New date for written exam "Angewandte Themen für das Informatik-Lehramt"Due to a collision with "Maschinelles Lernen 1", the written exam in "Angewandte Themen für das Informatik-Lehramt" is now on 13 March 2020 at 11:30PM, Bldg. 50.34, Room -101. |
 A Glimpse of the Matrix: Scabalitiy Issues of a New Message-Oriented Data Synchronization Middleware presented at ACM/IFIP International Middleware Conference A Glimpse of the Matrix: Scabalitiy Issues of a New Message-Oriented Data Synchronization Middleware presented at ACM/IFIP International Middleware ConferenceAt the 20th International Middleware Conference at UC Davis, California, we presented our poster A Glimpse of the Matrix: Scalability issues of a new message-oriented data synchronization middleware on 2019-12-11. We describe measurements of the public federation of the [matrix] network and discuss scalability issues of the current message routing mechanism. Additional details can be found in the Extended Tech Report. More images by @middleware2019 on twitter. |
 2019/09/26: TEE-Based Distributed Watchtowers for Fraud Protection in the Lightning Network presented on ESORICS CBT'19 2019/09/26: TEE-Based Distributed Watchtowers for Fraud Protection in the Lightning Network presented on ESORICS CBT'19At the 3rd International Workshop on Cryptocurrencies and Blockchain Technology (CBT'19) on 26th and 27th Septembre, 2019, co-located with ESORICS 2019 we presented our work "TEE-Based Distributed Watchtowers for Fraud Protection in the Lightning Network". We propose TEE Guard, a distributed watchtower solution for the Lightning Network that utilises Trusted Execution Environments. |
 2019/06/05: Outstanding Paper Award 2019/06/05: Outstanding Paper AwardOut conference submission "Access Control for Binary Integrity Protection using Ethereum" has been published in the respective proceedings. Furthermore, our contribution received the "Best Paper Runner Up" award. |
 2019/06/25: Awarding of the SICK-Wissenschaftspreis for master thesis on Bitcoin 2019/06/25: Awarding of the SICK-Wissenschaftspreis for master thesis on BitcoinThe SICK-Wissenschaftspreis for the best thesis 2017 was awarded to Matthias Grundmann for his master thesis titled "Analysis and Evaluation of Analysis Methods for Topology Inference in the Bitcoin Peer-to-Peer Network" at the annual Tag der Informatik. In this thesis he discussed possibilities for dertermining the topology of the Bitcoin peer-to-peer network and introduced two new methods to accomplish this. |
 2019/05/29: Banklaves: Concept for a Trustworthy Decentralized Payment Service for Bitcoin presented on IEEE ICBC'19 2019/05/29: Banklaves: Concept for a Trustworthy Decentralized Payment Service for Bitcoin presented on IEEE ICBC'19On the IEEE International Conference on Blockchain and Cryptocurrency from 14-17 May 2019 in Seoul, South Korea we presented our publication "Banklaves: Concept for a Trustworthy Decentralized Payment Service for Bitcoin", which explores a new way to implement a second layer architecture for cryptocurrencies using Trusted Execution Environments. |
 2019/05/30: Banklaves: Concept for a Trustworthy Decentralized Payment Service for Bitcoin presented on IEEE ICBC'19 2019/05/30: Banklaves: Concept for a Trustworthy Decentralized Payment Service for Bitcoin presented on IEEE ICBC'19On the IEEE International Conference on Blockchain and Cryptocurrency from 14-17 May 2019 in Seoul, South Korea we presented our publication "Banklaves: Concept for a Trustworthy Decentralized Payment Service for Bitcoin", which explores a new way to implement a second layer architecture for cryptocurrencies using Trusted Execution Environments. |
 2019/05/21: New Publication - Access Control for Binary Integrity Protection using Ethereum 2019/05/21: New Publication - Access Control for Binary Integrity Protection using EthereumIn the paper "Access Control for Binary Integrity Protection using Ethereum", we present a concept for representing and managing software on a public Blockchain, like Ethereum, for the purpose of integrity protection and revocation thereof. The work will be presented during the ACM Symposium on Access Control Models and Technologies (SACMAT) at the beginning of June in Toronto and will be available via KITOpen later. |
 2019/03/15: Registration to Courses in the Summer Term 2019 2019/03/15: Registration to Courses in the Summer Term 2019Registration to the ACS Practical Course as well as the Seminar "Hot Topics in Decentralized Systems" will open on the 1st of April at 2:00pm via the Wiwi-Portal. Further information can be found on the pages of the respective course. Edit: Registration for the Seminar was moved to Friday, 5th of April at 10:00am. |
 2019/01/28: 3rd ForDigital Blockchain Workshop 2019/01/28: 3rd ForDigital Blockchain WorkshopOn February 14th and 15th, 2019, the 3rd ForDigital Blockchain Workshop will take place at KIT. Researchers and practitioners in the field of Blockchains are invited to discuss challenges and opportunities of blockchain technologies and to talk about work currently being done. |
 2019/01/19: DSN Traveller in the favourite Matrix projects 2018 2019/01/19: DSN Traveller in the favourite Matrix projects 2018Ben Parson, Developer Advocate for Matrix.org, mentioned the DSN Traveller, which was developed in the group as part of the master's thesis of Florian Jacob, in his favourite Matrix projects 2018. |
 2019/01/07: New Publication - Towards Application of Cuckoo Filters in NSM 2019/01/07: New Publication - Towards Application of Cuckoo Filters in NSMIn the paper "Towards Application of Cuckoo Filters in Network Security Monitoring" we study the feasibility of applying the recently proposed cuckoo filters to improve space efficiency for set membership testing in Network Security Monitoring, focusing on the example of Threat Intelligence matching. The work was presented in November 2018 on the 14th International Conference on Network and Service Management (CNSM). |
 2018/11/30: Successful PhD graduation - Till Neudecker 2018/11/30: Successful PhD graduation - Till NeudeckerOn November 30th Till Neudecker successfully defended his dissertation. Congratulations! |
 2018/11/15: Thesis in Cooperation with IISM 2018/11/15: Thesis in Cooperation with IISMThe research group Information & Market Engineering headed by Prof. Weinhardt offers a cross-faculty thesis titled Dezentrales Handeln in Energiemärkten - Was kann die Blockchain [in German] starting January 2019, which will be co-supervised by us. The announcemend is aimed primarily at Master computer science students, but Bachelor students are also welcome to apply. |
 2018/10/22: KASTEL-Newsletter Q3 2018/10/22: KASTEL-Newsletter Q3We contributed two articles to the latest KASTEL-Newsletter (in German). In the column "Insights into our Research" (p. 19) we give, as the name implies, a generally comprehensible overview of one of our latest publications, and in the news section (p. 22) we report on the recent Bro Workshop Europe. |
 2018/09/19: Bro Workshop Europe 2018/09/19: Bro Workshop EuropeOn 18th and 19th of September our group hosted the first European Bro Workshop in cooperation with the International Computer Science Institute (ICSI). Bro is an open source network monitoring software project. |
 2018/09/07: New Publication - Atomic Information Disclosure of Off-Chained Computations Using Threshold Encryption 2018/09/07: New Publication - Atomic Information Disclosure of Off-Chained Computations Using Threshold EncryptionOur workshop submission Atomic Information Disclosure of Off-Chained Computations Using Threshold Encryption has been published in the Lecture Notes in Computer Science. |
 2018/09/10: New Publication - Network Layer Aspects of Permissionless Blockchains 2018/09/10: New Publication - Network Layer Aspects of Permissionless BlockchainsOur survey Network Layer Aspects of Permissionless Blockchains has been published by the IEEE Journal "Communications Surveys & Tutorials". |
| Neue Veröffentlichung: Network Layer Aspects of Permissionless Blockchains |
 2018/07/27: Exam IT-Sicherheitsmanagement (summer term 2018) 2018/07/27: Exam IT-Sicherheitsmanagement (summer term 2018)You cannot longer register for the exam. The exam will be held on August 1st, 2018 at 10:30am in "Redtenbacher-Hörsaal". More information can be found on the lecture's homepage. |
 2018/07/16: Bro Workshop Europe 2018/07/16: Bro Workshop EuropeOur group hosts the first European Bro Workshop in September of this year. Bro is an open source network monitoring software project. Read more. |
 2018/06/22: Award for the best application-related master thesis 2018/06/22: Award for the best application-related master thesisWe're happy to announce that in the context of the "Tag der Informatik 2018" the master thesis of Matthias Grundmann has been awarded with the prize for the best application-related master thesis. The prize was sponsored by Robert Bosch GmbH. |
 2018/04/26: PET-CON 2018.1 2018/04/26: PET-CON 2018.1On April 19th and 20th, 2018 the PET-CON 2018.1 took place in Berlin. The workshop was organized by the special interest group Privacy Enhancing Technologies of the Gesellschaft für Informatik. From the DSN group our staff members Marc Leinweber and Matthias Grundmann participated in the workshop. |
| 2018/04/26: Start of the ACS-Lab The ACS-Lab starts today (2018/04/26). The Lab takes place at 2pm in SCC's F-Pool. |
| 2018/04/23: CBT 2018 Am 6. und 7. September findet in Barcelona im Anschluss an die ESORICS 2018 der Internationale Workshop Cryptocurrencies and Blockchain Technologies unter Mitwirkung von Prof. Hartenstein statt. |
| 2018/04/10: SoK Seminar The first meeting of the SoK seminar takes place on April 23rd, 2018 at 2pm in room 314 of building 20.21 (SCC). |
| 2018/04/06: Information regarding second IT-Security Management exam The second exam for IT-Security Management takes place on Wednesday, 2018/08/01, at 10:30 AM in the Redtenbacher-Lecture Hall. Further details concerning (de-)registration will follow in time. |
| 2018/04/04: New homepage online! The homepage of the research group has been reworked and is now online in its new form. |

